Connecting devices that are far away to a central place can feel like a big puzzle, especially when you need everything to be safe and sound. When we talk about devices that sense and send information, often called Internet of Things or IoT things, getting them to chat with cloud services in a way that keeps their messages private is a real concern for many folks. This is where setting up a special kind of private space on the internet, specifically with Amazon Web Services or AWS, starts to make a lot of sense for handling those remote connections. It is a way, you see, to build a secure bridge for all your scattered gadgets.
Think about all the different gadgets out there, from sensors checking soil moisture in a field to cameras watching a distant factory floor, or even smart meters reading energy use in homes across a city. These devices need a reliable way to send their bits of information back to a central brain for analysis or action. Sending this data over the public internet, while common, might not always give you the peace of mind you want regarding who else might be listening in or if the information could get messed with. That is why creating a dedicated, private connection for these remote IoT things becomes a very good idea, indeed.
This idea of a private connection often brings us to something called a Virtual Private Cloud, or VPC, particularly when we are talking about services provided by AWS. A VPC is essentially your own little section of the AWS cloud, completely cut off from other users unless you specifically say otherwise. It is like having your own private office building within a huge office park. When you combine this private cloud space with the needs of remote IoT devices, you get a setup that helps keep your device communications isolated and secure, which, you know, is pretty important for sensitive information. Basically, it helps keep your secrets safe.
- Ssh Raspberry Pi Iot Projects
- Ryder Evan Russaw
- Beth Thomas
- Sarah Levy Husband
- What Age Was Justin Bieber When He Sang Baby
Table of Contents
- What is a Remote IoT VPC Network on AWS?
- Why bother with a private setup for Remote IoT?
- Getting started with your Remote IoT VPC Network on AWS
- Keeping your Remote IoT VPC Network on AWS running smoothly
What is a Remote IoT VPC Network on AWS?
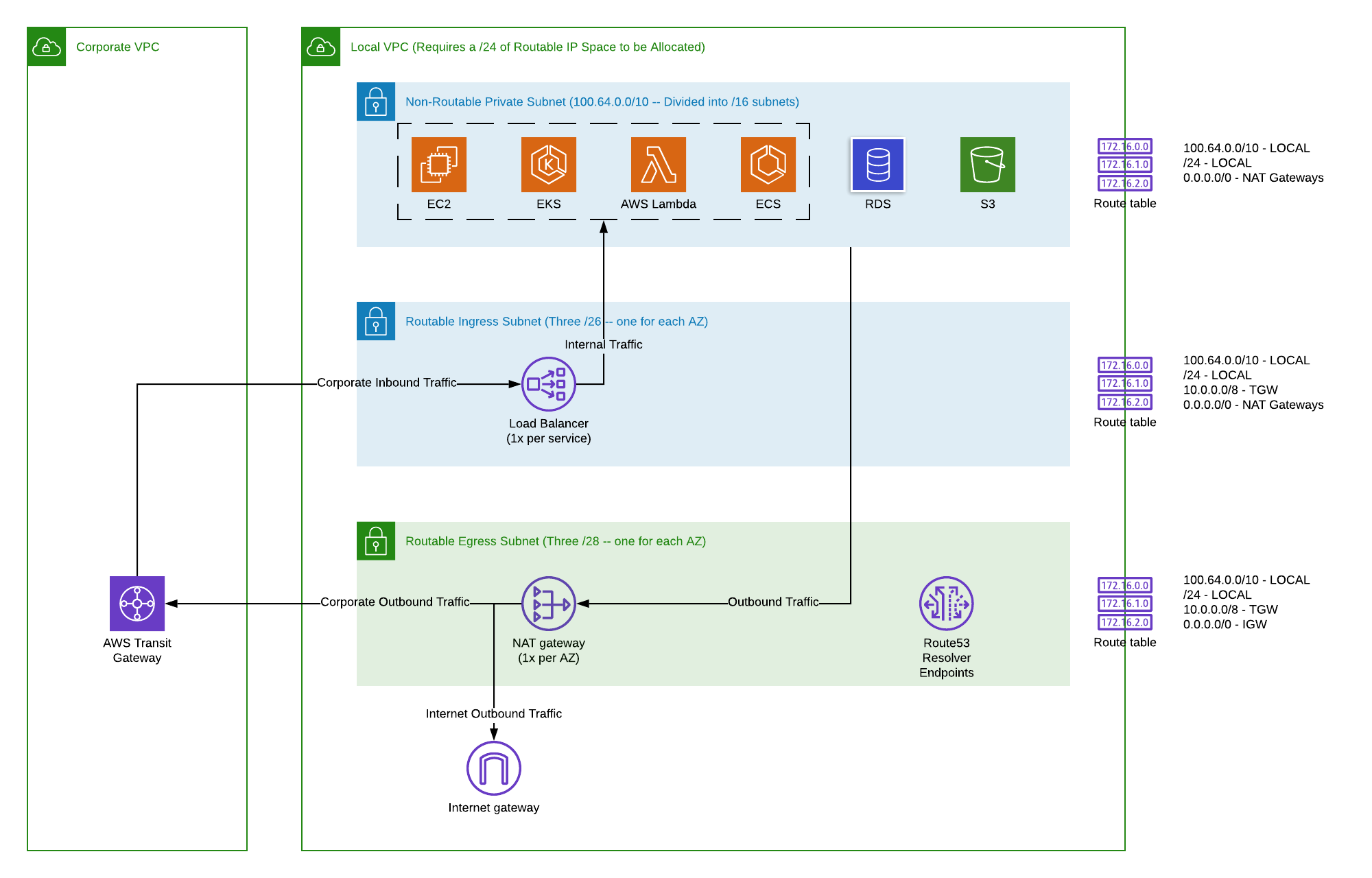
A Remote IoT VPC Network on AWS is, put simply, a private digital space you create within Amazon's cloud services specifically for your internet-connected devices that are located far away. Think of it like building a private road directly from your distant devices to your main data center in the cloud, rather than having them travel on the very busy public highway. This private road means that the information your devices send and receive stays within your controlled environment, protected from the general internet traffic. It is almost like having a dedicated phone line just for your gadgets, you know, making sure no one else can listen in on the conversation. This setup helps keep everything neat and tidy.
This private area, the VPC, gives you a lot of control over who can access your device data and what kinds of connections are allowed. You can set up specific rules, like digital bouncers, to decide which traffic gets in and which stays out. This is pretty different from just sending data over the open internet, where you have less say over the path your information takes. For things like industrial sensors or medical devices, where data privacy and integrity are very important, having this kind of isolated connection is, well, pretty much a must. It gives you a sense of calm, knowing your information is in its own walled garden.
The idea here is to make sure your remote devices, no matter where they are physically, can communicate with your AWS services as if they were sitting right next to them in a secure office. This means you can gather data, send commands, and manage your devices without worrying as much about outside interference. It is like having a direct, secure line for all your important device chatter. That, in a way, is the core benefit of this kind of setup. You get peace of mind, which is worth a lot.
How does a Remote IoT VPC Network on AWS connect devices?
Connecting devices in a Remote IoT VPC Network on AWS usually involves a few steps to make sure the path is both private and functional. First, your remote devices need a way to reach the internet, typically through a local internet connection like Wi-Fi or cellular data. Once they are online, they do not just connect directly to your VPC. Instead, they often use a secure tunnel, something like a Virtual Private Network (VPN) connection or a direct private link, to get into your private cloud space. This tunnel acts as a secret passage, making sure the data travels securely from the device to your AWS VPC. It is, you know, a bit like a secret handshake before entering a private club.
Inside your AWS VPC, you set up specific services that are ready to receive and process the data from your devices. This might include things like AWS IoT Core, which is a service specifically for managing and connecting IoT devices, or other computing services that run your applications. These services are placed within your private VPC, meaning they are not directly exposed to the public internet. So, when your remote device sends data through its secure tunnel, it arrives directly into this private area, where only your authorized services can see and use it. This setup, frankly, keeps everything very contained and safe.
For the connection to work, you also need to set up rules within your VPC to allow this specific traffic. These rules are like security checkpoints that only let authorized vehicles pass. You might use something called security groups or network access control lists (NACLs) to define exactly which types of data and from which sources are allowed into your private network. This layered approach means that even if someone tried to send something unauthorized, your VPC would likely block it before it could reach your important services. It is, as a matter of fact, a pretty thorough way to keep things locked down.
Why bother with a private setup for Remote IoT?
Many folks might wonder why go through the extra effort of setting up a private network for remote IoT devices when the public internet seems to work just fine for many things. The main reason, quite simply, comes down to security and control. When your devices send sensitive information, like health data, financial transactions, or operational details from a factory, you really want to be sure that data is not intercepted or altered by unauthorized parties. Using a private setup like a VPC on AWS gives you a much tighter grip on who can see and interact with your device communications. It is, in a way, like putting your valuables in a safe deposit box instead of leaving them out in the open.
Beyond just security, a private network also offers better performance and reliability for your device communications. When you are not competing with all the other traffic on the public internet, your data can often travel faster and more consistently. This is especially important for applications where timing is critical, like controlling machinery or responding to alerts in real-time. A dedicated path means less chance of delays or dropped connections, which, you know, can be pretty frustrating when you are trying to keep things running smoothly. This kind of setup just works better for those demanding tasks.
Another big benefit is the ability to manage your network resources more effectively. Within your private VPC, you have complete say over the IP addresses, subnets, and routing tables. This allows you to design a network structure that perfectly fits the needs of your remote IoT devices and applications. You can segment your network, for instance, putting different types of devices or applications into their own isolated sections. This kind of organization makes it easier to troubleshoot problems, apply updates, and scale your operations as your device fleet grows. It is, essentially, about having your own private playground where you set all the rules.
What makes a Remote IoT VPC Network on AWS secure?
The security of a Remote IoT VPC Network on AWS comes from several layers working together, like a well-guarded castle. First, the very nature of a VPC means it is logically isolated from other AWS customers. Your private cloud space is yours alone, and traffic generally cannot flow into or out of it without your explicit permission. This isolation is a fundamental building block of its security, providing a kind of digital moat around your data. It is, actually, a pretty good start for keeping things private.
Within this private space, you have powerful tools to control access. Security Groups act like firewalls for individual services or groups of services, allowing you to specify exactly which types of incoming and outgoing traffic are permitted. For example, you might only allow your IoT services to communicate with specific ports and protocols, blocking everything else. Network Access Control Lists (NACLs) provide another layer of defense at the subnet level, giving you even finer control over network traffic. These tools together are like having multiple checkpoints, ensuring only approved visitors can get in. That, you know, is pretty important for sensitive data.
Furthermore, AWS offers services that help secure the connection from your remote devices into the VPC itself. Options like AWS Site-to-Site VPN or AWS Direct Connect establish encrypted tunnels, meaning all the data traveling between your devices and your VPC is scrambled and unreadable to anyone who might intercept it. This encryption protects your data while it is in transit, a bit like sending a sealed letter that only the intended recipient can open. This combination of isolation, granular access control, and encrypted communication makes a Remote IoT VPC Network on AWS a very secure place for your device data, which is, honestly, a huge plus.
Getting started with your Remote IoT VPC Network on AWS
Getting your own Remote IoT VPC Network on AWS up and running might seem like a big project at first, but it can be broken down into smaller, manageable steps. The first thing you will want to do is plan out your network address space. This means deciding on the range of private IP addresses your VPC will use. Think of it like assigning house numbers in a new neighborhood; you want enough numbers for all your current and future residents, and you want to make sure they do not overlap with other neighborhoods. This initial planning, you know, helps prevent headaches later on. It is a bit like mapping out your journey before you leave.
After you have a good plan for your IP addresses, you will create the VPC itself within the AWS management console. This is where you actually draw the boundaries of your private cloud space. Once the VPC is created, you will then divide it into smaller sections called subnets. Subnets are useful for organizing your resources and applying different security rules to different parts of your network. For instance, you might have one subnet for your IoT data processing services and another for your databases, each with its own set of access rules. This separation, frankly, makes things much more organized and secure.
The next part involves setting up internet gateways or VPN connections. An internet gateway allows your VPC to communicate with the public internet, which is necessary if your devices need to connect from outside your direct private link. If you are using a VPN, you will configure that connection to establish the secure tunnel from your remote devices into your VPC. You will also need to set up routing tables, which tell your network traffic where to go, ensuring that data from your remote devices reaches the correct services within your VPC. This step, basically, ensures all the roads lead to the right places.
What are the main parts of a Remote IoT VPC Network on AWS?
When you put together a Remote IoT VPC Network on AWS, several key pieces come into play, each with its own job. At the very core is the VPC itself, which is your isolated section of the AWS cloud. This is the foundation upon which everything else is built, providing that private space for your operations. Without it, you are pretty much just sending data over the open internet, which is not what we are aiming for here. It is, you know, the main building of your private compound.
Inside the VPC, you have subnets. These are smaller segments of your VPC's IP address range. You typically divide your VPC into multiple subnets, perhaps one for public-facing resources (if you need any) and others for private resources like databases or sensitive application servers. This allows you to control traffic flow and security at a finer level. For instance, you might have a private subnet where your AWS IoT Core services live, completely cut off from direct public access. This separation, you see, is a big part of keeping things secure.
Then there are the security controls, like Security Groups and Network Access Control Lists (NACLs). Security Groups are like virtual firewalls that control traffic to and from individual instances or services, while NACLs operate at the subnet level, controlling traffic in and out of entire subnets. These are absolutely vital for making sure only authorized data can enter or leave your private network. They are, in a way, the guards at the gates, checking everyone who comes and goes. This is pretty much how you keep things safe.
Finally, you have the connectivity options. This includes things like Internet Gateways for public internet access (if needed for certain device interactions or management), and VPN connections or AWS Direct Connect for establishing secure, private links from your remote IoT devices back into your VPC. These connections are the pathways that allow your distant devices to communicate with your private cloud environment. They are, essentially, the secure tunnels that bring all your remote data home. This setup, you know, helps everything work together smoothly.
Keeping your Remote IoT VPC Network on AWS running smoothly
Once your Remote IoT VPC Network on AWS is set up, the job is not quite done. Keeping it running well means a bit of ongoing attention, like tending to a garden. You will want to regularly check on your network's performance, making sure data is flowing as expected and that there are no unexpected slowdowns. AWS provides monitoring tools that can help you keep an eye on things, giving you alerts if something seems off. This regular check-in, you know, helps catch small problems before they become big ones. It is a bit like doing routine maintenance on your car.
Security is also an ongoing task. As new threats emerge or as your device fleet changes, you might need to adjust your security group rules or NACLs. Regularly reviewing who has access to your VPC and what permissions they have is also a good practice. Think of it like updating the locks on your doors or changing your alarm codes periodically. Staying on top of security updates and best practices from AWS is also a very good idea to keep your network protected against the latest vulnerabilities. This constant vigilance, frankly, helps keep your digital fortress strong.
Scaling your network as your number of remote IoT devices grows is another consideration. Your VPC should be designed with future expansion in mind, perhaps with enough IP address space to accommodate new devices without having to completely redesign your network. You might also need to add more VPN connections or increase the bandwidth of your existing ones as your data volume increases. This forward thinking, you see, helps avoid disruptions as your operations expand. It is about making sure your network can grow with you, which is pretty important for long-term success.
Thinking about costs for your Remote IoT VPC Network on AWS
When you are setting up and running a Remote IoT VPC Network on AWS, it is only natural to think about the money side of things. The good news is that AWS has a pay-as-you-go model, meaning you generally only pay for the services you actually use. This can be very helpful for managing your budget, as you are not locked into large upfront costs. However, it also means you need to understand what parts of your setup will add to your monthly bill. This careful planning, you know, helps avoid any surprises when the invoice arrives.
Some of the main cost factors include the data transfer fees. While data moving within your VPC is often free or very low cost, data that moves in and out of AWS, especially over the public internet, can incur charges. This includes data sent from your remote IoT devices into your VPC if it is coming from outside AWS's network. The amount of data your devices send, and how often they send it, will therefore play a big role in your overall expenses. It is, basically, like paying for gas on a long trip; the more you drive, the more you pay.
Other costs might come from the specific AWS services you use within your VPC to process your IoT data. Services like AWS IoT Core, compute instances (like EC2 virtual servers), databases, and storage all have their own pricing structures. The more resources you use, and the longer you use them, the higher your costs will be. Additionally, if you are using dedicated VPN connections or AWS Direct Connect, there might be charges associated with those private links themselves. Keeping an eye on your usage through AWS's billing dashboard can help you manage these expenses effectively. This kind of monitoring, you see, is pretty much essential for staying on budget.
Setting up a Remote IoT VPC Network on AWS offers a strong way to connect your distant devices privately and securely. This approach helps keep your data safe, provides better control over your network, and supports reliable communication for all your internet-connected gadgets. By understanding the core parts of a VPC, how devices connect, the security benefits, and the associated costs, you can build a solid foundation for your IoT operations.
Related Resources:


Detail Author:
- Name : Torrance Cruickshank PhD
- Username : ernest36
- Email : bechtelar.mertie@hotmail.com
- Birthdate : 2007-06-17
- Address : 3675 Fahey Island New Wilhelmberg, OR 30160-4449
- Phone : 1-336-857-3865
- Company : VonRueden Group
- Job : Photographic Restorer
- Bio : Voluptatum accusamus sunt aut quaerat sed maiores. In vel ducimus id voluptatem adipisci consequatur possimus aliquid. Eos et sit eos velit repellendus minima.
Socials
twitter:
- url : https://twitter.com/carmenkozey
- username : carmenkozey
- bio : Error quam culpa unde omnis. Fugiat vero sed sed voluptatem magnam et. Deserunt sint saepe illo. Fuga corrupti quaerat eum. Repudiandae quia soluta ab.
- followers : 1677
- following : 1667
facebook:
- url : https://facebook.com/ckozey
- username : ckozey
- bio : Dolor voluptatibus dolor nisi beatae. Quia minima animi eum.
- followers : 4951
- following : 44